Fortinet Firewall Training by Experts
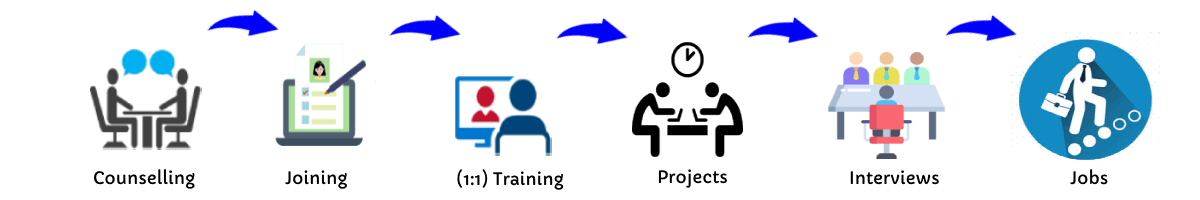
Our Training Process
Fortinet Firewall - Syllabus, Fees & Duration
MODULE 1
- System setup
- Fort guard subscription services
- Logging
- Firewall policies
- Policies
- Policies lab
MODULE 2
- Firewall
- Firewall types
- How to control access
- Managing firewall
- NAT
- Denial of service (DoS)
MODULE 3
- Basic VPN
- VPN uses, advantages and types
- Need of firewall in VPN
- Threat free tunneling
- VPN Bandwidth management
- SSL VPN
- SSL VPN with RADIUS and forti token
- SSL VPN using web and tunnel mode
- Dialup IPsec VPN
MODULE 4
- Authentication
- Requirement and types of authentication
- Group authentication
- Traffic discovery
- AD, LD AP, OR RADIUS
MODULE 5
- Antivirus
- Functioning of Anti-Virus & Anti-Spam
- Basics of Virus, Spyware, Malware, Phishing, and Pharming.
- Web/Mail/FTP Anti-Virus
- Gateway level Anti-Virus/Anti-Spam
- Instant Messaging
- Virus Outbreak Detection
- Recurrent Pattern Detection
- RBL, IP Reputation
- Understanding of Intrusion
- Signature-based detection
- Statistical anomaly-based detection
- Stately protocol analysis detection
- Network-Based IPS & Wireless Based IPS
- Network Behaviour Analysis
- Host-Based IPS
MODULE 6
- Spam filtering
- Web filtering
- Need for web filtering
- Web 2.0 filtering
- Filtering with keywords, URL
- Filtering web traffics
MODULE 7
- Application firewall
- Evolution of Application Firewall
- File Filtering
- Application & P2P Filtering
- Instant Messaging Filters
- Custom Filters
- Compliance based filtering
MODULE 8
- WiFi
- Wifi settings
- Wifi MAC filter
- Wifi monitoring
MODULE 9
- Network availability
- High availability
- Load balancing
- Understand balancing
- Multilink manager
- Active-Active load balancing and gateway failover
- Active – Passive configuration and gateway failover
- MPLS failover to VPN
- Automatic ISP failover detection
This syllabus is not final and can be customized as per needs/updates




 According to the latest Anti-Phishing Working Group (APWG) report, SSL was employed by 75% of all phishing sites in the first quarter of 2020.
Understand the responsibilities of encryption and certificates.
Examine SSL/TLS-protected communication for evidence of encryption being used to circumvent security restrictions.
This will necessitate a wide range of capabilities, including high-performance decryption, post-decryption deep packet inspection, detection of malicious URLs, identification of command and control operations, malware download, and threat correlation.
Firewall policies are used to control network access to configured networks.
Use port forwarding, source NAT, and destination NAT to your advantage. These features, however, are CPU-intensive and are known for bringing even high-end commercial NGFWs to a halt.
Firewall policies are used to authenticate users.
Identify the Fortinet Security Fabric's features.
The networking landscape of today is more sophisticated than it has ever been.
According to the latest Anti-Phishing Working Group (APWG) report, SSL was employed by 75% of all phishing sites in the first quarter of 2020.
Understand the responsibilities of encryption and certificates.
Examine SSL/TLS-protected communication for evidence of encryption being used to circumvent security restrictions.
This will necessitate a wide range of capabilities, including high-performance decryption, post-decryption deep packet inspection, detection of malicious URLs, identification of command and control operations, malware download, and threat correlation.
Firewall policies are used to control network access to configured networks.
Use port forwarding, source NAT, and destination NAT to your advantage. These features, however, are CPU-intensive and are known for bringing even high-end commercial NGFWs to a halt.
Firewall policies are used to authenticate users.
Identify the Fortinet Security Fabric's features.
The networking landscape of today is more sophisticated than it has ever been.